Vishvesh Shah
プロダクト・マネジメント・ディレクター
IIoTデバイスのシームレスでセキュアなリモートソフトウェア管理を実現します。リトマスエッジマネージャが、セキュアで一元化された自動ソフトウェア配布により、IIoTデバイスのOTAアップデートを簡素化する方法をご覧ください。
IT teams and digital transformation advocates will find the Syslog Server connector in Litmus Edge particularly beneficial for its ability to effortlessly merge IT & OT data streams, improving real-time decision-making across intricate networked systems.
In the complex and diverse architecture of modern IT infrastructures, Syslog has become an indispensable tool. Syslog plays a pivotal role in network management, security, compliance, and enhancing operational efficiency by collecting, storing, and analyzing log messages from numerous network devices and software applications. They serve as the backbone for understanding and reacting to system behaviors across an organization's IT infrastructure.
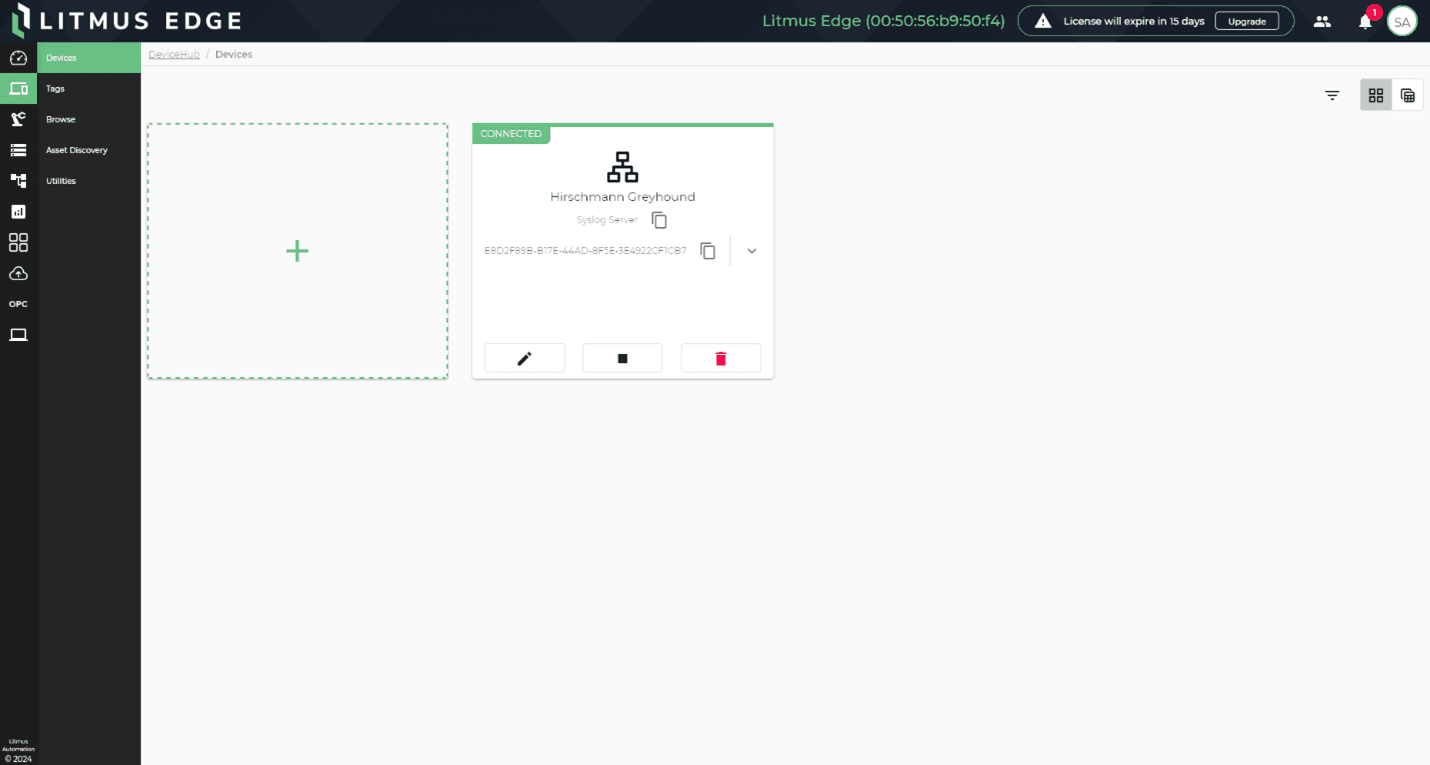
Litmus Edge has integrated a Syslog server into DeviceHub, enabling it to read data from Syslog clients in various IT equipment and correlate it with the operational technology data already being collected from PLCs and other industrial devices. This addition positions the Syslog server as one component within DeviceHub, alongside several other native industrial connectors, most of which are dedicated to OT or industrial applications. In pursuit of our objective to offer a holistic industrial data operations platform that caters to both OT and IT needs, there's no longer a necessity to engage a distinct IT vendor solely for collecting these logs from switches. This function can now be efficiently managed with Litmus Edge.
The Syslog Server connector is available at no additional cost in the Litmus Edge UI – just like the rest of the native connectors. Users, having access to this data within DataHub, can engage in tracking, tracing, and exploring other potential use cases. For instance, they can correlate observed anomalies with similar incidents from network equipment, enhancing the understanding of underlying challenges. The integration of Syslog with the other DeviceHub protocols was strategically planned to facilitate such comprehensive analyses.
Generally, networks switches are located within the OT or IT level. OT switches are often quite aged, having been supplied by industrial vendors. As such, they may not support Syslog for anomaly reporting, and their functionalities are typically embedded directly within the PLC code. PLC error logs, crucial for identifying anomalies, are typically generated within the PLC code and can be translated by SCADA and HMI systems. These logs allow for the development of analytics codes or applications specifically designed for error mapping. On the other hand, with the ongoing convergence of OT and IT, switches are now being managed mostly by IT. This is leading to an emergence of IT logs that are instrumental for auditing, system management, and infrastructure management. Users can now leverage these logs using the Syslog Server in Litmus Edge.
For digital transformation strategists or enterprise data users, the integration of IT and OT connectivity becomes pivotal. Now users have the option to transmit this data to the cloud for correlation analysis, or they can perform real-time mapping directly at the edge. This means actively correlating data, such as if an anomaly is detected in the PLC, it could be associated with networking issues identified at the same timestamp.
Let’s take a quick look at some of the most common use cases of a Syslog server.
Centralized Log Collection
It aggregates logs from various sources, allowing for centralized monitoring and management. This includes routers, switches, firewalls, servers, and any device or application with a Syslog client. Centralization simplifies log management, especially in complex IT environments.
Log Storage and Retention
Syslog servers store these logs for a predefined period, aiding in compliance with data retention policies and regulations. This historical log data can be crucial for audits and forensic analysis.
Log Analysis, Monitoring, and Troubleshooting
It helps in real-time monitoring of network health and security. By analyzing the log messages, Syslog servers can trigger alerts based on predefined criteria, such as potential security breaches, system errors, or configuration changes. The collected logs provide valuable insights that assist in diagnosing and solving network and system issues. They offer context and details about events leading up to a problem.
Compliance and Auditing
Many industries have regulations requiring the collection and retention of logs for compliance purposes (e.g., GDPR, HIPAA, SOX). A Syslog server helps in maintaining these records in an organized and accessible manner. The logs serve as an audit trail for changes, access, transactions, and events across the network. This is essential for security audits, investigations, and compliance checks.
Security
In the event of a security incident, the detailed logs contained within a Syslog server are invaluable for forensic analysis, helping to identify the cause and scope of an attack. By analyzing log data over time, Syslog servers can assist in detecting unusual patterns that may indicate a security threat or system misuse.
Considering the requirements of modern infrastructure, we will continue to add new integrations and connectors natively to Litmus Edge enabling a future-ready, single source of truth for both IT and OT teams. Stay tuned to try this driver in our latest release.
For more exciting product updates and feature enhancements, sign up on the Litmus Central Portal and be the first to try them out. Get started today or schedule your personalized demo with our technical team.
Parth Desai
ソリューション&インダストリアル・ディレクター
パース・デサイはリトマスの創業エンジニアであり、インダストリアル&ソリューションズチームを率いる。
Vishvesh Shah
プロダクト・マネジメント・ディレクター
IIoTデバイスのシームレスでセキュアなリモートソフトウェア管理を実現します。リトマスエッジマネージャが、セキュアで一元化された自動ソフトウェア配布により、IIoTデバイスのOTAアップデートを簡素化する方法をご覧ください。
Parth Desai
リトマス、ソリューション&インダストリアル・ディレクター/ファウンディング・エンジニア
リトマスでは、お客様からいただくフィードバックに共通のテーマがあります。同じ生産ラインの同じ機械であっても、すべての矛盾やばらつきがある生の工業データをどのように理解すればよいのでしょうか?
Archana Punnoose
Sr. Product Manager, Litmus
急速に進化する産業用モノのインターネット(IIoT)では、エッジデバイス間の通信チャネルのセキュリティが最も重要です。